Access codes are used to protect information and functions by controlling who can read, write, and execute them. They ensure that only authorized individuals can view, modify, or run certain data and programs.
In this case, these codes function like locks placed on a field in a screen, within a transaction, in a report, or on a database record. They ensure that only authorized users can access, modify, or execute specific parts of the system.
Building on this, access to protected information is managed by defining specific permissions for each user. This way, users have the necessary “key” to unlock the information. These permissions are set in the user record, allowing the assignment of rights to read, write, and/or execute specific data or functions. An “All Access Codes” checkbox allows certain users to bypass restrictions and access all information protected by access codes. This grants them full read, write, and execution permissions across the system.
This entry is made in a scrolling grid, where only the access codes are entered. The format of these codes is flexible and can be customized as needed.
- This tab contains the following fields:
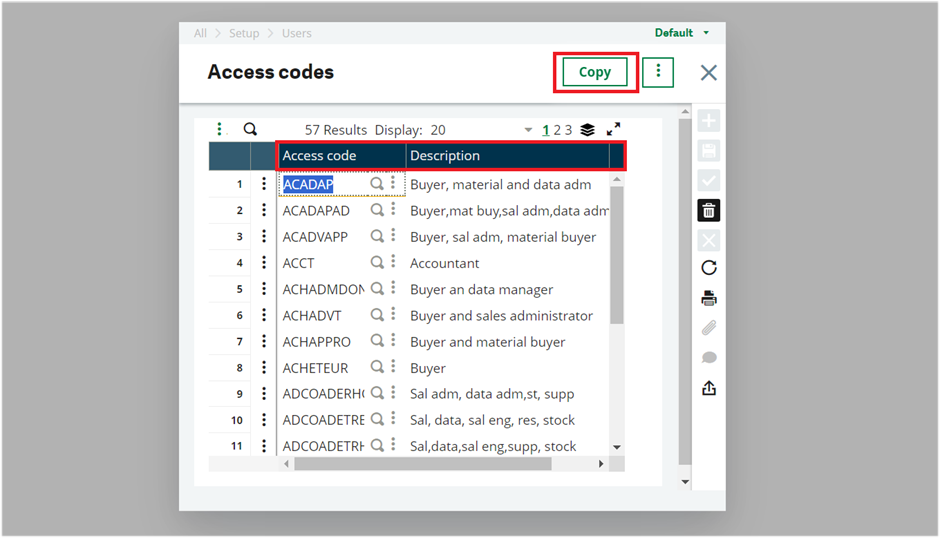
Fig 1: Access code
- Access Code (field CODACC): This code uniquely identifies the current record.
- Description (field DESACC): It specifies the description of the Access codes.
- Copy (Button): This button copies all access codes to another folder. It only creates codes that do not already exist in the target folder, and it does not affect any existing codes in the target folder.
Use of access codes
Access codes can be entered into various functions, whether during development or while managing database elements within the software.
The standard functionality, controlled by object management, works as follows: When a file includes an access code, object management filters rights for displaying and modifying each record. This is based on the access code entered in the record and the user’s permissions for reading and writing associated with that access code.
This feature automates basic access rights management for standard records where access codes are used. It also simplifies the addition of specific filters across all object management. Simply adding an access code field to a screen or table associated with an object, and declaring it in the Access Code section of object management, enables these filtering capabilities.
Supervisor objects in the table utilize access code filters for reading and writing. When an object’s code is present in bold, access codes are also tested during execution, with detailed rights specified later in the document.
Execution rights for the bolded objects above are managed as follows:
- Access codes in setup transactions restrict their use unless users have been granted execution rights.
- Access codes in requests prevent their execution unless the user has been granted execution rights.
- Access codes in system transactions prevent their execution unless the user has been granted execution rights.
- Access codes in inquiry screens restrict their use unless the user has been granted execution rights.
Access codes can be associated with fields on screens using the allocation function. The user’s read and write rights for each code determine whether the field can be displayed or modified.
Each software package based on X3 technology uses access codes to control database access and software operations.

